China Cross-Border Data Transfer Compliance
Navigate China’s cross-border data transfer regulations with confidence.
Protect your business, ensure compliance, and enable global operations.
Why Is Data Export Compliance Critical?
- Legal Requirement: China’s Personal Information Protection Law (PIPL) and Data Security Law strictly regulate cross-border data transfers. Non-compliance can result in severe penalties.
- Business Continuity: Data export compliance is essential for global operations, cloud adoption, and serving international customers from China.
- Reputation & Trust: Demonstrating compliance builds trust with partners, clients, and regulators worldwide.
- Risk Mitigation: Avoid fines, business suspension, and reputational damage from unauthorized data transfers.
- Competitive Advantage: Compliance enables smoother business with multinational clients and partners.
China’s Cross-Border Data Transfer Legal Framework
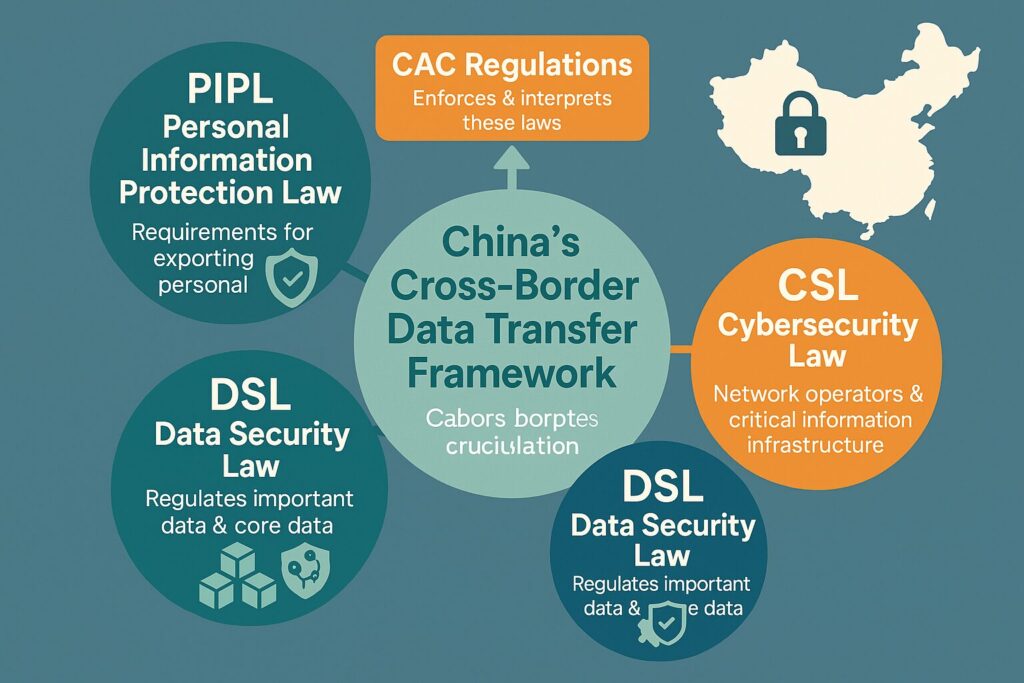
- Personal Information Protection Law (PIPL): Sets strict requirements for exporting personal data outside China.
- Data Security Law (DSL): Regulates important data and national core data transfers.
- Cybersecurity Law (CSL): Covers network operators and critical information infrastructure.
- CAC Regulations: The Cyberspace Administration of China (CAC) enforces and interprets these laws, issuing detailed rules and guidelines.
main legal pathways for cross-border data transfer compliance
- Cross Border Data Transfer Assessment: Required for large-scale or sensitive data exports, or if exporting important data.
- Standard Contract: For most routine personal data exports, a CAC-approved contract must be signed and filed.
Common Scenarios Requiring Data Export Compliance
- Using global cloud or SaaS platforms (e.g., Salesforce, AWS, Microsoft 365)
- Remote access to Chinese systems by overseas staff or partners
- Transferring HR, customer, or business data to headquarters or affiliates abroad
- International e-commerce, logistics, or payment processing
- Cross-border R&D, analytics, or support operations
Key Requirements for Data Export from China
- Conduct a Personal Information Protection Impact Assessment (PIPIA) before any cross-border transfer.
- Obtain clear, informed consent from data subjects for export of personal information.
- Choose and implement the correct legal pathway: government assessment, standard contract, or certification.
- File documentation and contracts with the Cyberspace Administration of China (CAC) as required.
- Implement robust technical and organizational safeguards for data security and privacy.
Step-by-Step Data Export Compliance Process

- Scenario Assessment: Identify data flows, business scenarios, and legal requirements.
- Impact Analysis: Conduct a PIPIA and document risks and mitigation measures.
- Pathway Selection: Determine if a government assessment, standard contract, or certification is required.
- Remediation: Address gaps in security, privacy, and documentation.
- Filing & Approval: Submit required documents to CAC or relevant authorities and obtain approval if needed.
- Ongoing Monitoring: Maintain compliance and update assessments as business or regulations change.
Navigating these requirements can be complex—our experts help you choose the right pathway, prepare documentation, and ensure smooth, compliant data flows.
Risks of Non-Compliance
- Fines up to 50 million RMB or 5% of annual revenue
- Business suspension or license revocation
- Loss of trust and reputational damage
- Legal action and criminal liability for responsible individuals
Frequently Asked Questions
Q:
Is the data collected from China?
A:
- data processor is not restricted to entities registered in China. It applies to anyone who provide service to China that collects data from China.
- Intermediate data, not processed in China is not applied
Q:
Define Cross-Border Transfer
A:
- Incl. :
- Server hosted outside of China and company in China input data via client or browser
- Data are stored in China and sending/synchronized to Headquarter, or HQ can read/access the data on demand, but data still hosted in China.
- Hongkong, Macao and Taiwan where required Exit & Entry Administration are all considered to be out of China
- Data Transfer to Rep. Office of foreign companies also apply
Q:
What should companies do? Assessment @CAC OR/AND Personal Information Standard Contract?
A:
The rule presents two options, one being “Assessment,” if all the criteria are met, while the other is the standard contract for personal information. However, the standard contract alone is insufficient for compliance with cross-border data transfer; it only applies when companies transfer personal information and do not meet the conditions of the “Assessment.” On the other hand, the “Assessment” alone is also insufficient; companies must also conclude the standard contract when transferring personal information.
Q:
Who can use standard contract?
A:
(1) a data processor who transfers Important Data abroad;
(2) NOT a critical information infrastructure operator, or a data processor processing the personal information of more than 1 million individuals, who, in either case, transfers personal information abroad;
(3) NOT a data processor who has, since January 1 of the previous year cumulatively transferred abroad the personal information of more than 100,000 individuals, or the sensitive personal information of more than 10,000 individuals, or
(4) other circumstances where the security assessment for the outbound data transfer is required by the State Cyberspace Administration.
Summarize: Data processor who do NOT meet the requirement of assessment.
Q:
Is the standard contract enough without the assessment @CAC?
A:
- NO, the rule means not the standard contract is the only necessary part of the cross-border data transfer. The assessment should still be done if the data processor meets the requirement of the “rule”.
- Vice versa.
- Therefore, we recommend to take both.
How We Help
- Expert guidance on China’s data export laws and best practices
- Impact assessment and documentation support
- Remediation planning and implementation
- Government filing and communication
- Ongoing compliance management
Would you like to learn more about our cross-border data transfer service?
You can make an appointment with us for an on-site discussion, or we can come to your company for an on-site inspection, to jointly explore your security needs.
