MLPS 评估
摘要:
自2019年以来,新的多层次保护计划(MLPS)2.0标准已经发布,现在它越来越多地从政府实体进入企业。本文是针对主要企业进行MLPS评估或如何使企业尽可能符合MLPS标准的指导。

由于国家安全立场的发展,以及网络犯罪在中国发生的越来越频繁,为了保护中国经济和中国人民的生计,中国于2017年6月发布了网络安全法(《中华人民共和国网络安全法》,即CSL)。《电信企业法》第21条规定,所有网络运营者均应履行MLPS。
MLPS是帮助网络运营商对其信息系统/网络进行评级和维护和保护的规范性文件。
自2008年以来,MLPS已经起草并实施。它首先被认为是专门为政府实体保护国家网络安全。但在2017年之后,如CSL所述,所有网络运营商(包括重点工业公司,甚至外商独资企业)都有义务遵循MLPS标准,以保护其运营的网络。
1.1.法律参考
- 《中华人民共和国网络安全法》
- 中华人民共和国计算机信息系统安全保护条例(中华人民共和国国务院令(第147号))
- 《信息安全多层次保护管理办法》(工同字[2007]43号)
1.2.标准
- GB/T 22239-2019《信息安全技术多层次保护基本要求》
- GB/T 25070-2019《信息安全技术网络安全多级防护安全设计技术要求》
- GB/T 28448-2019《信息安全技术网络安全多层次保护评估要求》
- GB/T 25058-2019《信息安全技术-网络安全分类保护实施指南》
1.3.对象:网络运营商
本规范的分级对象是指建设、运营和使用基础信息网络、云计算平台/系统、大数据应用/平台/资源、物联网、工业控制系统和采用移动互联网技术的系统、承载独立业务应用的数据资源和信息系统的地方政府部门、企事业单位或具有代表性的其他社会组织。
网络运营者应当按照多层次保护制度的要求,履行安全义务,确保网络不受干扰、破坏、不被非法接入,防止网络数据泄露、被盗用、伪造。
2.评估程序
2.1.一般流程
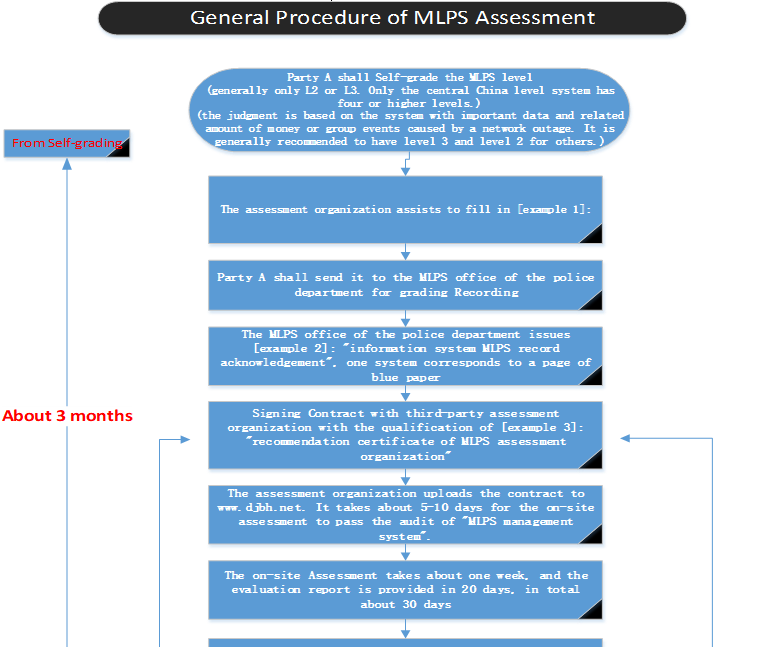
2.1.1.示例1 “MLPS记录表”,由评估机构提供。

2.1.2.例2 《MLPS备案证书》,由公安部门出具。

2.1.3.例3“MLPS评估机构推荐证书”

2.1.4.例4 “评估报告”
2.2.自动分级
网络运营商根据自己的网络/系统情况填写申请表(模板表格见附件1,因为只接受中文表格,所以我们没有翻译)。
采取哪一级是基于下面的矩阵:
| Harmed objects when the network/system is damaged | Severity of the harm | ||
|---|---|---|---|
| harm | serious harm | particularly serious damage | |
| legitimate rights and interests of the Chinese citizens | L1 | L2 | L3 |
| social order and the public interest | L2 | L3 | L4 |
| National Security | L3 | L4 | L5 |
当网络拓扑、用途、服务范围/对象或处理的数据发生变化时,相应的安全级别也应重新分级。
根据我们的经验,通常对于制造公司来说,最大L2就足够了。甚至L1也是可以接受的。
由于2021年的新形势,目前我们区域内所有对外商独资企业自我评级2级以上的认可都不成功。这意味着外商独资企业可以在没有得到官方评估的情况下为MLPS做好准备。
2.3.现场评估
评估机构将申请表交予市网络安全保障局(见附件2),市网络安全保障局办公室邀请三名或三名以上专家进行审查,并通知区网络安全警察参加评估会议。
评估开始前,参加评估的专家应选择一名专家作为评估工作的负责人,由组长主持评审会。
申请人的负责人应当将网络和信息系统的基本情况向审核组报告具体的网络和信息系统情况,包括但不限于:
1.主体的责任:
(1)信息系统的规划设计、立项、开发建设、运行时间;
(2)项目主管、开发单位、系统集成与安全集成商、网络设备及安全产品供应商、安全服务提供商(含运维)等;
(3)系统所在服务器机房、负责部门、用户部门等。
2.系统功能的应用:
(1)系统所使用的编程语言和数据库管理软件,以及版本;
(2)本系统设置的应用服务器的数量、品牌、型号和数量、数据库类型和数据库服务器的数量;
(3)系统的主要功能;
(4)系统是否提供在线服务;
(5)是否有手机应用;
(6)系统是否采用了大数据、云计算等。
(7)用户类型和数量。
如果现场无法演示,请将各功能页面截图制作成演示文件。
3.系统网络结构:
(1)系统的网络架构;
(2)出站连接数和带宽;
(3)部署在网络边界的核心网设备;
(4)安全防护产品情况(注明品牌、型号);
(5)保安设备的政策和状况;
(6)简要介绍网络结构、区域和边界的定义以及安全方法等。
4.数据的情况:
(1)系统收集的数据(包括公民个人信息)的大小、类型以及安全保护方式的收集、存储、传输、使用、提供、销毁等方面;
(2)是否向第三方提供数据接口(如有),请清楚描述;是否签署了保密协议;
(3)从核心数据中收集了哪些字段,总量是多少;
(4)收集公民个人信息的字段(包括手机号码、身份证)及其总量。
(5)简要介绍主要数据类型、数量以及如何存储它们。
5.自评分情况及原因:
介绍申请人系统的保安级别,并解释建议级别的相关级别。如果有更好的指导,请召集专家组。介绍申请人系统的保安级别,并解释建议级别的相关级别。如果有更好的指导,请召集专家组。
6.专家评价:
评估专家根据申请人申报情况,采用询问、查阅资料等方式对拟应用信息系统的水平进行评审。
评估内容包括但不限于以下内容:
(1)审核责任主体:通过询问、查阅文件等形式,检查申请人是否对分级信息系统的安全主管负有责任。
(2)审查评级对象:通过询问、查阅资料和现场观看等方式,审查评级对象是否具备信息系统的三个基本要素:明确责任主体;相对独立的业务应用;多个互联资源。避免将单个系统组件(如服务器、终端、网络设备等)作为分级对象;
(3)审查客体和来自客体的损害影响:通过网络运营者提供的材料,在专家意见中说明清楚网络和信息系统客体和来自客体的损害影响的原因。
7.评估结果:
现场评估完成后,由组长的专家共同确定申请人评分对象的合理性,并由所有专家签名(避开现场评分对象申请人)。
在评估过程中,如发现分级对象存在重大安全隐患,应在评估意见结束时提出建议,便于网络运营者及时整改。
3.评价项目
3.1.Level 2
Security Category Security sub-category Number of assessment items Comments
Physical security Selection of physical location 1 Evaluate whether the physical server room is in the building with the ability of shockproof, windproof and rainproof
Physical access control 2 The examination and approval control means of entering and leaving the server room and the entrance and exit of the server room need to be attended by special personnel
Theft and vandalism 5 Evaluate the security of equipment and communication cables in the server room and the anti-theft alarm facilities.
Lightning protection 2 Evaluate the construction of building lightning protection and induction lightning protection and AC power ground wire
Fire prevention 1 Evaluate the setting of automatic monitoring fire protection system and the fire-fighting equipment.
Waterproof and damp proof 3 Evaluate the water pipe setting, rainwater infiltration, condensation and underground water transfer and infiltration in the server room.
Antistatic 1 Evaluate the anti-corrosion measures of key equipment.
Temperature and humidity control 1 Evaluate the temperature and humidity control measures of the server room.
Power supply 2 Evaluate the power supply line voltage stabilization, overvoltage and standby power supply in the server room.
Electromagnetic protection 1 Evaluate the isolation of power line and communication cable
Total 19
Network security Structural safety 4 Main verification: the processing capacity of key network equipment, whether the network bandwidth meets the business requirements, whether the network topology is consistent, and whether the subnet is divided.
Access control 4 Main verification: border network device access control function, system and dial-up access restrictions.
Security audit 2 Main verification: network equipment log collection, and audit records detailed records.
Boundary integrity check 1 Main verification: whether it can check the behavior of unauthorized devices connecting to the internal network.
Intrusion Prevention 1 Main verification: deployment and usage of IDS.
Network equipment protection 6 Main verification: user identification, administrator login address restriction, user identity uniqueness, password policy, login policy, remote management policy.
Total 18
Host security Identification 5 Main verification: user identification method, account and user correspondence, account and password length setting, password change cycle, etc; Login failure handling function settings.
Access control 4 Main verification: privilege separation of privileged users; Access right of default account; Processing of redundant and overdue accounts.
Security audit 4 Main verification: coverage of safety audit; Record content integrity; Prevent audit records from being deleted and covered.
Intrusion Prevention 1 Main verification: operating system component installation and patch upgrade.
Malicious code prevention 2 Main verification: use and upgrade of anti-virus and malicious code products. Support the unified management of anti malware software.
Resource control 3 Main verification: terminal login restriction mode and security policy
Total 19
Application Security Identification 4 Main verification: identity identification and authentication, authentication information complexity, login failure processing function and user identity uniqueness check, etc.
Access control 4 Main verification: independent access control function, minimum required authority and mutual restriction.
Security audit 3 Main verification: coverage of safety audit; Record content integrity; Prevent audit records from being deleted and covered.
Communication integrity 1 Main verification: Communication cryptography technology ensures the integrity of data communication process.
Communication confidentiality 2 Main verification: whether to use cryptographic technology for session initialization verification and encryption of sensitive information in the communication process.
Software fault tolerance 2 Main verification: data validation; Whether the fault can provide some functions.
Resource control 3 Main verification: automatic end session function, maximum number of Concurrent Session connections limit, multiple concurrent sessions limit for a single account.
Total 19
Data security Data integrity 1 Main verification: identify the integrity of information and important business data in the transmission process.
Data confidentiality 1 Main verification: use encryption or other protection measures to identify the storage confidentiality of information.
Backup and recovery 2 Main verification: backup and recovery of important information; Hardware redundancy of network equipment.
Total 4
Safety management system Management system 3 Main verification: overall security strategy construction; Establish safety management system for important management contents in safety activities; Establishment of personnel management operation procedures.
Development and release 3 Main verification: the establishment of the responsible department for the formulation of the safety management system; Establishment, review and release of safety management system.
Review and revision 1 Main verification: review and revision of safety management system
Total 7
Post setting 2 Main verification: establishment of safety management posts and clarification of responsibilities.
Staffing 2 Main verification: staffing of safety management posts.
Authorization and approval 2 The main verification is to authorize the approval department and the approving person according to the responsibilities of each department and post; The approval process for key activities shall be established and signed by the approval person.
Communication and cooperation 2 Main verification: communication and cooperation among management personnel, internal organizations and information functional departments; Cooperation and communication among brother units, public security organs and telecommunication companies.
Audit and inspection 1 Main verification: standardization and implementation of system safety inspection.
Safety management organization Total 9
Personnel safety management Personnel recruitment 3 Main verification: standardized management of personnel recruitment process; Sign the confidentiality agreement for the employed personnel.
Personnel leaving post 3 Main verification: control of personnel departure process;
Personnel assessment 1 Main verification: conduct safety skill and safety cognition assessment for each daring personnel.
Safety awareness education and training 3 Main verification: formulation and implementation of safety training plan.
Access management of external personnel 1 Main verification: approval and supervision of external personnel entering important areas. And grade record.
Total 11
System construction management System grading 3 Main verification: whether the security protection level of the information system is clear, and the method and reason for determining the security protection level in written form, to ensure that the grading results are approved by relevant departments.
Security scheme design 4 Main verification: the overall planning and design of the information security work of the system.
Purchase and use of products 3 Main verification: purchase and use management measures of information security products in the system.
Self developed software 3 Main verification: management of self-development of software within the system
Outsourcing software development 4 Main verification: the quality of outsourcing software to ensure the safety and availability of outsourcing software.
Project implementation 2 Main verification: implementation of information system engineering.
Test acceptance 3 Main verification: acceptance of information system engineering.
System delivery 3 Main verification: delivery of information system engineering.
Security service provider selection 3 Main verification: selection of relevant security service providers and service management measures in the system.
Total 28
System operation and maintenance management Environmental management 4 Main verification: daily management of server room infrastructure and office environment.
Asset management 2 Main verification: asset list preservation measures; Establish asset safety management system.
Media management 4 Main verification: storage, filing, destruction and classified management measures of various media.
Device management 4 Main verification: management of daily use, operation and maintenance of all kinds of equipment.
Network security management 6 Main verification: Construction of safety management system and inspection of illegal networking.
System security management 6 Main verification: system access control, patch, daily vulnerability scanning and audit management.
Malicious code prevention management 3 Main verification: the management of malicious code detection, analysis and other preventive work.
Password management 1 Main verification: the institutionalization and implementation of password use.
Change management 2 Main verification: the institutionalization of change activities and the standardized management before, during and after the change.
Backup and recovery management 3 Main verification: daily backup management of system data and system recovery management.
Security incident handling 4 Main verification: the construction of security incident reporting and disposal system and the standardized management of different security incident handling processes.
Emergency plan management 2 Main verification: formulate emergency plans for different events and train system idlers on emergency plans.
Total 41
Total 66 items 175 indexes
3.2.Level 3
| Security Category | Security sub-category | Number of assessment items | Comments |
|---|---|---|---|
| Physical security | Selection of physical location | 2 | Evaluate whether the physical server room is in a building with the ability of shockproof, windproof and rainproof |
| Physical access control | 4 | The examination and approval control means of entering and leaving the server room and the entrance and exit of the server room need to be attended by special personnel | |
| Theft and vandalism | 6 | Evaluate the security of equipment and communication cables in the server room and the anti-theft alarm facilities | |
| Lightning protection | 3 | Evaluate the construction of building lightning protection and induction lightning protection and AC power ground wire | |
| Fire prevention | 3 | Evaluate the setting of automatic monitoring fire protection system and the fire-fighting equipment | |
| Waterproof and damp proof | 4 | Evaluate the water pipe setting, rainwater infiltration, condensation and underground water transfer and infiltration in the server room | |
| Antistatic | 2 | Evaluate the anti-static measures of main equipment | |
| Temperature and humidity control | 1 | Temperature and humidity control measures of assessment room | |
| Power supply | 4 | Evaluate the power supply line voltage stabilization, overvoltage and standby power supply in the server room | |
| Electromagnetic protection | 3 | Assessment of electromagnetic interference and electromagnetic protection | |
| Total | 32 | ||
| Network security | Structural safety | 7 | Main verification: processing capacity of main network equipment, whether network bandwidth meets business requirements, whether network topology is consistent, subnet division and isolation, bandwidth priority allocation of important services |
| Access control | 8 | Main verification: border network equipment access control function, system and dial-up access restrictions, information content filtering in and out of the network, maximum network traffic and connections, and measures to prevent address deception | |
| Security audit | 4 | Main verification: network equipment log collection, detailed records of audit records, audit report generation and protection measures for audit records | |
| Boundary integrity check | 2 | Main verification: whether the unauthorized equipment can be connected to the internal network independently to check, locate and block; Check, locate and block the behavior of internal users’ private external connection | |
| Intrusion Prevention | 2 | Main verification: deployment and usage of IDS | |
| Malicious code prevention | 2 | Main detection: detection and removal of malicious code at the network boundary | |
| Network equipment protection | 8 | Main verification: user identification, administrator login address restriction, user identity uniqueness, password policy, login policy, remote management policy and user authority separation | |
| Total | 33 | ||
| Host security | Identification | 6 | Main verification: user authentication method, account and user correspondence, account and password length settings, password change cycle, etc; Login failure handling function settings |
| Access control | 7 | Main verification: privilege separation of privileged users; Access right of default account; Disposal of surplus and overdue accounts | |
| Security audit | 6 | Main verification: coverage of safety audit; Record content integrity; Prevent audit records from being deleted and covered | |
| Residual information protection | 2 | Main inspection: the clearance of user identification information, system files, directories and data in the storage space | |
| Intrusion Prevention | 3 | Main verification: operating system component installation and patch upgrade, intrusion behavior record and alarm, and recovery measures after damage | |
| Malicious code prevention | 3 | Main verification: usage and upgrade of anti-virus and malicious code products, unified management of anti malicious code software, and malicious code library different from network anti malicious code products | |
| Resource control | 5 | Main verification: terminal login restriction mode and security policy, monitoring server resource usage and minimum alarm measures | |
| Total | 32 | ||
| Application Security | Identification | 5 | Main verification: identity identification and authentication, complexity of user name and password, whether to use two or more combination of authentication technologies, login failure processing function and uniqueness check of user identity |
| Access control | 6 | Main verification: the function of independent access control, the minimum required authority and the relationship of mutual restriction, the function of setting sensitive marks on important information resources and controlling the operation of important information resources with sensitive marks | |
| Security audit | 4 | Main verification: coverage of safety audit; Record content integrity; Prevent audit records from being deleted and covered; Functions of security audit statistics, query, analysis and audit report generation | |
| Residual information protection | 2 | Main inspection: the clearance of user identification information, system files, directories and data in the storage space | |
| Communication integrity | 1 | Main verification: Communication cryptography technology ensures the integrity of data communication process | |
| Communication confidentiality | 2 | Main verification: whether to use cryptographic technology for session initialization verification and encrypt the whole message or session process in the communication process | |
| Non-Repudiation | 2 | Main inspection: the function of providing primary evidence and receiving evidence of data | |
| Software fault tolerance | 2 | Main verification: data validation; Whether it can provide partial function and automatic protection function in case of failure | |
| Resource control | 7 | Main verification: automatic end session function, maximum concurrent session connection number limit, multiple concurrent session limit of a single account, maximum and minimum resource allocation of a single account, alarm function of reaching the minimum value, service priority setting function | |
| Total | 31 | ||
| Data security | Data integrity | 2 | Main verification: integrity of user account information and important business data in the transmission process |
| Data confidentiality | 2 | Main verification: use encryption or other protection measures to ensure the storage confidentiality of user account information and important business data | |
| Backup and recovery | 4 | Main verification: backup and recovery of important information; Hardware redundancy of network equipment | |
| Total | 8 | ||
| Safety management system | Management system | 4 | Main verification: overall security strategy construction; Establish safety management system for important management contents in safety activities; Personnel management operating procedures establish and form a comprehensive information security management system composed of security strategy, management system and operating procedures |
| Development and release | 5 | Main verification: the establishment of the responsible department for the formulation of the safety management system; The formulation, audit and release of safety management system, whether there is a unified format and version control | |
| Review and revision | 2 | Main verification: review and revision of safety management system and safety management system | |
| Total | 11 | ||
| Safety management organization | Post setting | 4 | Main verification: safety management department, post establishment and clear responsibilities |
| Staffing | 3 | Main verification: staffing of safety management posts | |
| Authorization and approval | 4 | The main verification is to authorize the approval department and the approving person according to the responsibilities of each department and post; The approval process for important activities shall be established and signed by the examiner | |
| Communication and cooperation | 5 | Main verification: communication and cooperation among management personnel, internal organizations and information functional departments; Cooperation and communication among brother units, public security organs and telecommunication companies; Establish contact list of external units and employ information security experts as perennial security consultants | |
| Audit and inspection | 4 | Main verification: standardization and implementation of system safety inspection, regular and comprehensive inspection | |
| Total | 20 | ||
| Personnel safety management | Personnel recruitment | 4 | Main verification: standardized management of personnel recruitment process; Signing confidentiality agreement for employed personnel; Key post personnel sign post safety agreement |
| Personnel leaving post | 3 | Main verification: personnel departure process control | |
| Personnel assessment | 3 | Main verification: carry out safety inspection, strict safety review and skill assessment for all post personnel, and keep assessment results and records | |
| Safety awareness education and training | 4 | Main verification: formulation and implementation of safety training plan | |
| External personnel access management | 2 | Main verification: approval and supervision of external personnel entering important areas, and filing at different levels | |
| Total | 16 | ||
| System construction management | System grading | 4 | Main verification: whether the information system defines its security protection level and the method and reason for determining the security protection level in written form, ensures that the grading results are approved by relevant departments, and whether experts are organized to demonstrate and approve |
| Security scheme design | 5 | Main verification: the overall planning and design of the system’s information security work | |
| Purchase and use of products | 4 | Main verification: purchase and use management measures of information security products in the system | |
| Self developed software | 5 | Main verification: management of self software development in the system | |
| Outsourcing software development | 4 | Main verification: the quality of outsourcing software, to ensure the safety and availability of outsourcing software | |
| Project implementation | 3 | Main verification: implementation of information system engineering | |
| Test acceptance | 5 | Main verification: acceptance of information system engineering | |
| System delivery | 5 | Main verification: delivery of information system engineering | |
| System record | 3 | Main verification: record of information system | |
| Grade assessment | 4 | Main verification: assessment and rectification of information system | |
| Security service provider selection | 3 | Main verification: selection of relevant security service providers and service management measures in the system | |
| Total | 45 | ||
| System operation and maintenance management | Environmental management | 4 | Main verification: daily management of server room infrastructure and office environment |
| Asset management | 4 | Main verification: asset list preservation measures; Establish asset safety management system, classify and mark assets | |
| Media management | 6 | Main verification: establish media security management system, take measures for storage, filing, destruction and classification management of various media, and take encryption measures for data and software in important media | |
| Device management | 5 | Main verification: establish equipment maintenance management system to manage the daily use, operation and maintenance of all kinds of equipment | |
| Monitoring management and safety management center | 3 | Main inspection: take monitoring and management measures to monitor and alarm the communication line, host, network equipment and application software; Establish a security management center to centrally manage equipment status, malicious code, patch upgrade, security audit and other security related matters | |
| Network security management | 8 | Main verification: Construction of safety management system and inspection of illegal networking | |
| System security management | 7 | Main verification: system access control, patches, daily vulnerability scanning and audit management | |
| Prevention and management of malicious code | 4 | Main verification: the management of malicious code detection, analysis and other preventive work | |
| Password management | 1 | Main verification: the institutionalization and implementation of password use | |
| Change management | 4 | Main verification: institutionalized construction of change activities and standardized management before, during and after change | |
| Backup and recovery management | 5 | Main verification: daily backup management of system data and system recovery management | |
| Security incident handling | 6 | Main verification: the construction of security incident reporting and handling system and the standardized management of different security incident handling processes | |
| Emergency plan management | 5 | Main verification: formulate emergency plans for different events, train relevant personnel of the system, and conduct regular drills, etc | |
| Total | 62 | ||
| Total | 73 items | 290 indexes |
3.3.MLPS高危项目及整改办法
| NO. | Security Category | Security Sub-Category | Level-2 rectification | Level-3 rectification | Investment | |
|---|---|---|---|---|---|---|
| 1 | Physical security | 1 | Selection of physical location | |||
| 2 | 2 | Physical access control | Electronic access control | Medium | ||
| 3 | 3 | Theft and vandalism | Video monitoring system / burglar alarm system | Video monitoring system / burglar alarm system | Medium | |
| 4 | 4 | Lightning protection | lightning protector | Low | ||
| 5 | 5 | Fire prevention | Fire-fighting equipment and automatic fire alarm system | Automatic fire-fighting system | High | |
| 6 | 6 | Waterproof and damp proof | Dehumidifier | Waterproof detection and alarm | Medium high | |
| 7 | 7 | Antistatic | Anti-static floor | Medium | ||
| 8 | 8 | Temperature and humidity control | Precision air conditioner | Precision air conditioner | High | |
| 9 | 9 | power supply | Voltage regulator, overvoltage protection equipment, UPS | Voltage regulator, overvoltage protection equipment, UPS, standby power supply system | High | |
| 10 | 10 | Electromagnetic protection | Electromagnetic shielding and electromagnetic interference device | Low | ||
| 11 | Network security | 1 | Structural safety | Core equipment redundancy | Medium | |
| 12 | 2 | Access control | Border firewall | Border firewall | Medium high | |
| 13 | 3 | Security audit | Log audit system | Log audit system | Medium | |
| 14 | 4 | Boundary integrity check | Private external connection control (terminal security management system) | Network access control / private external connection control (terminal security management system) | Medium | |
| 15 | 5 | Intrusion Prevention | Intrusion detection / defense system | Intrusion prevention system | Medium | |
| 16 | 6 | Malicious code prevention | Network anti virus gateway | Medium | ||
| 17 | 7 | Network equipment protection | Network operation and maintenance management system (Jumper machine) | Medium | ||
| 18 | Host security | 1 | Identification | Multi factor identity authentication system | Medium | |
| 19 | 2 | Access control | Host security environment system | Medium | ||
| 20 | 3 | Security audit | Log audit system | Log audit system | Medium | |
| Database audit system | Database audit system | |||||
| 21 | 4 | Residual information protection | Host security environment system | Medium | ||
| 22 | 5 | Intrusion Prevention | Patch management system (free WSUS or terminal management system with patch management module) | Host intrusion prevention software / patch management system (free WSUS or terminal management system patch management module) | Medium | |
| 23 | 6 | Malicious code prevention | Network version antivirus software | Network version anti-virus software (host anti malicious code products should have different malicious code libraries from network anti malicious code products) | Medium | |
| 24 | 7 | Resource control | Security monitoring center host system resource monitoring module | |||
| 25 | Application Security | 1 | Identification | Multi factor identity authentication system | Medium | |
| 26 | 2 | Access control | ||||
| 27 | 3 | security audit | Application system audit module configuration | Log integrated audit system application audit module / application system audit module configuration | Medium | |
| 28 | 4 | Residual information protection | ||||
| 29 | 5 | Communication integrity | ||||
| 30 | 6 | Communication confidentiality | ||||
| 31 | 7 | Non-Repudiation | Digital certificate | |||
| 32 | 8 | Software fault tolerance | Web Application Firewall | Web application firewall / webpage tamper proof system | Medium | |
| 33 | 9 | Resource control | Security monitoring center application system resource monitoring module | Medium | ||
| 34 | Data security and backup | 1 | Data integrity | Data transmission integrity protection / data storage integrity protection (data security protection system) | Medium | |
| 35 | 2 | Data confidentiality | Data transmission encryption / data storage encryption (data security protection system) | Medium | ||
| 36 | 3 | Backup and recovery | Local data backup and recovery system (full backup once a day), communication line and hardware redundancy, remote data backup and network structure redundancy | High | ||
| 37 | System operation and maintenance management | 1 | Monitoring management and safety management center | Environmental monitoring system (such as power distribution, UPS, air conditioning, temperature and humidity, water leakage, smoke, video, access control, fire protection system, etc.) | Medium | |
| 38 | 2 | Safety monitoring center (such as: monitoring and alarming of communication line, host, network equipment and application software, network traffic, user behavior, etc.) | Medium | |||
| 39 | 3 | Security Management Center (such as centralized management of equipment status, malicious code, patch upgrade, security audit and other security related matters) | Medium | |||
| Summary | There are 66 assessment items and 175 assessment indexes | There are 73 assessment items and 290 assessment indexes | ||||
4.总结
根据我们的经验,大多数没有任何web服务的中小企业制造商将处理/收集民用信息或为公众服务,通过MLPS二级评估没有问题。他们中的大多数都有内部系统,如MES/ERP,专门用于内部使用,并且已经具有强大的身份验证和安全方法。如果所有的高风险项目都被涵盖,那么通过它将不会是一个适当的报告的问题。中小企业生产企业无需申请三级,其成本仅为评估成本,收益较少。
对于无法通过评估的网络/主机项目,如防火墙/杀毒软件在现代IT环境中被广泛部署,特别是对于外商独资企业。IDS/IPS功能通常集成在防火墙系统中;日志审计器可以被任何syslog服务器确认。由于该品牌/型号目前未被列入白名单/黑名单。任何类似的设备都可以实现该功能。
在物理方面,没有良好服务器机房环境的中小企业,基于云的环境,如微软Azure 21Vnet,中国电信云/iDC已经通过MLPS认证。如果有环境监控系统对UPS电池、温度、湿度进行监控,将会有所帮助。
对于管理方面,已经编写好的灾难恢复计划将是最有帮助的,不仅对通过MLPS,而且对其自身的业务连续性也是如此。
5.Annex
1.Annex1_SelfGrading_网络安全等级保护定级报告
2.Annex2_MLPS_RecordForm网络安全等级保护备案表




