## Introduction
With rapid advancements in artificial intelligence technology, Agentic AI is transforming enterprise automation. Unlike traditional chatbots, Agentic AI can autonomously or semi-autonomously perform multi-step complex tasks, serving as a powerful engine driving digital transformation. However, as businesses rapidly deploy customized AI agents, they face increasingly severe security challenges. This article delves into the core concepts of Agentic AI and focuses on best practices and defense strategies for securing AI agents, empowering security teams to build strong defenses and achieve both business and innovation goals.
—
## What is Agentic AI and Its Role in Enterprise Automation?
Agentic AI refers to intelligent agents capable of autonomous decision-making, distinct from traditional passive chatbots. These AI agents not only understand instructions but can automatically complete multi-step task chains, greatly enhancing the efficiency and flexibility of business process automation. According to Gartner, over 53% of enterprises have deployed customized AI agents, significantly driving the intelligent automation wave.
For example, a large financial institution uses Agentic AI to manage customer identity verification processes, automatically detecting anomalies and responding swiftly, reducing processing time by 30%. Additionally, AI-assisted automation in cross-departmental approval workflows reduces human errors and delays.
However, due to their automation privileges and complex operations, Agentic AI expands the attack surface; traditional defense mechanisms cannot fully cover these new risks. Understanding Agentic AI’s essence and the responsibilities it carries in business environments is critical for security teams.
—
## Security Challenges and Attack Surface Analysis of Agentic AI
### Diverse Security Challenges
Agentic AI broadens the attack surface with key risks such as:
– Access control weaknesses: AI agents often require access to multiple system resources, and lax permission boundaries make them vulnerable to malicious exploitation.
– Unauthorized execution risks: Attackers may use prompt injection or jailbreak attacks to trick AI agents into executing unauthorized commands.
– Lack of intent recognition: AI agents operate by “executing instructions” without understanding intent, making them susceptible to damage if malicious commands pass through.
### Future Trends and Threat Predictions
Gartner predicts that by 2029, over 50% of successful attacks will exploit AI agent access control vulnerabilities. Attackers might leverage complex social engineering, credential theft, or insider abuse to trigger high-risk operations.
### Typical Attack Case
A well-known retailer’s AI agent, due to improper configuration and lack of least privilege enforcement, was exploited via jailbreak attacks to bypass security limits, resulting in massive customer data theft and manipulation of automated ordering processes, causing significant financial losses.
Hence, protecting Agentic AI begins with strong access control as the cornerstone of security.
—
## Best Practices for Agentic AI Security: Building a Zero Trust Defense
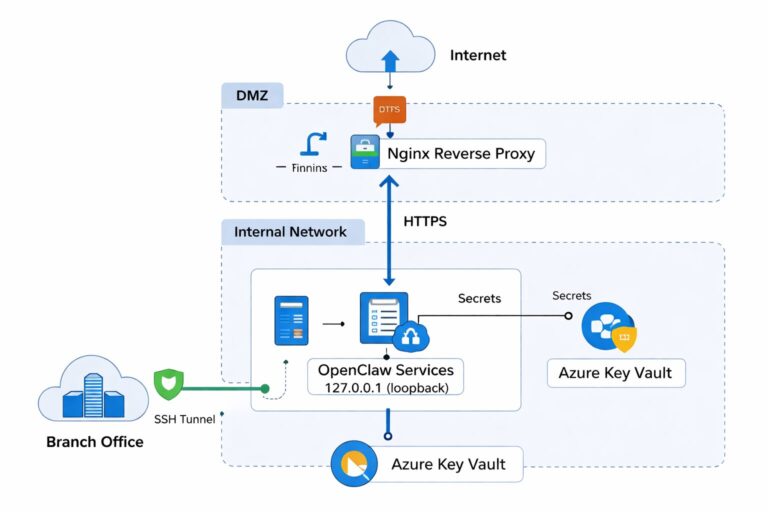
### 1. Modern Privileged Access Management (PAM) Platforms
Implement least privilege principles via PAM platforms to finely authorize and dynamically approve AI agent credentials. Key measures include:
– Centralized secure vault management of AI agent credentials.
– Execution approval workflows per invocation to ensure legal and safe operations.
– Comprehensive auditing of all access details for traceability and accountability.
For example, a multinational company uses Azure Privileged Identity Management (PIM) to set approval thresholds for sensitive AI agent operations, effectively preventing credential misuse.
### 2. Graduated Autonomy
Design tiered approval strategies based on risk levels:
– Low-risk operations (e.g., status checks, data listings): automatic approvals to enhance efficiency.
– High-risk operations (e.g., creating or deleting credentials): mandatory manual approval or multi-factor authentication.
This strategy ensures smooth automation while reducing the risk of errors, balancing security and flexibility.
### 3. Fine-grained Policies and Auditable Controls
Develop detailed policies incorporating multi-dimensional identity and temporal factors to make dynamic decisions:
– Set auto-approval rules based on agent identity, operation type, and time window.
– Real-time monitoring and logging ensure all operations are traceable and reversible.
For instance, an insurance company detects anomalies through real-time Agent behavior monitoring and automatically blocks potential unauthorized operations, greatly enhancing security.
—
## Agentic AI Security Deployment Process and Recommendations
### Asset Discovery and Attack Surface Assessment
Thoroughly map all AI agents’ access points and interaction flows to identify potential risk areas, serving as a basis for defense strategy.
### Threat Modeling and Security Testing
Simulate various attack scenarios such as prompt injection and unauthorized invocation to proactively discover vulnerabilities and defense blind spots.
### Runtime Protection Mechanisms
Deploy real-time policy enforcement engines integrating AI-driven attack detection and anomaly alerts to ensure AI agents’ secure runtime.
This dynamic, lifecycle-wide security management approach is key to achieving zero trust architectures.
—
## Key Factors for Successful Agentic AI Security Implementation
– **Early governance:** Embed zero trust principles at the design and deployment stages to avoid explosive risks later.
– **Innovation and control balance:** Promote business transformation with AI while establishing solid security defenses to prevent management barriers.
– **Team collaboration:** Security teams, AI developers, and business units must coordinate continuously through communication and training to build consensus and protective habits.
Only through comprehensive coordination can enterprises truly turn Agentic AI potential into secure and reliable business assets.
—
## FAQ
**Q1: What fundamentally distinguishes Agentic AI from traditional chatbots?**
A1: Traditional chatbots respond passively, whereas Agentic AI autonomously executes multi-step tasks enabling complex automation.
**Q2: Why is access control central to Agentic AI security?**
A2: AI agents hold cross-system operational permissions; weak access control leads to sensitive resource misuse, unauthorized actions, and data leaks.
**Q3: How does graduated autonomy enhance AI security?**
A3: By setting different approval levels for operations, low-risk tasks auto-approved for efficiency, high-risk tasks require manual approval to ensure safety.
**Q4: Why are traditional security mechanisms inadequate against Agentic AI threats?**
A4: Traditional mechanisms target static permissions and simple processes, failing to address AI agent’s multi-step, dynamic decision-making and complex attack vectors.
**Q5: How can enterprises conduct Agentic AI security testing?**
A5: By simulating prompt injection, privilege escalation, and other attacks combined with automated tools for continuous assessment and patching.
**Q6: How does zero trust operate throughout the Agentic AI lifecycle?**
A6: It enforces least privilege, fine-grained access controls, and dynamic monitoring from design, development, deployment to runtime, ensuring comprehensive protection.
—
By deeply understanding Agentic AI’s working mechanisms and security challenges and leveraging modern privileged access management, graduated autonomy, and fine-grained policies, enterprises can effectively reduce risks and ensure business continuity and data security.
For more AI security automation solutions, please visit De-Line Information Technology’s official website: [https://www.de-line.net](https://www.de-line.net), exploring new directions in intelligent security.
Let us jointly build a secure Agentic AI future and achieve technology-driven business innovation! 🚀✨
************
The above content is provided by our AI automation poster