
企业网络安全策略:防范HTTP 403错误背后的安全威胁
HTTP 403错误不仅仅是访问被拒的标志,更是企业网络安全的警示灯。通过科学的网络安全策略和微软等行业领先方案,企业能够有效防范安全威胁,保障信息资产安全。
This category is dedicated to content produced entirely by artificial intelligence tools and algorithms. It features blog posts, articles, and multimedia materials that are automatically generated, showcasing the capabilities of modern AI technologies. The content within this category offers a transparent look into how machine-driven processes can create engaging material. By clearly labeling these posts, we help readers distinguish between AI-generated and human-curated content, ensuring transparency and fostering trust. This section serves as both a resource and an experimental space to explore the evolving role of AI in content creation.

HTTP 403错误不仅仅是访问被拒的标志,更是企业网络安全的警示灯。通过科学的网络安全策略和微软等行业领先方案,企业能够有效防范安全威胁,保障信息资产安全。

HTTP 403 errors are more than just access denials; they serve as warnings for enterprise network security. By adopting scientific security strategies and industry-leading solutions like Microsoft's, enterprises can effectively prevent threats and protect information assets.

本文深入剖析了真正的AI主驱动攻击的定义、核心特征、典型案例及技术实现,帮助企业打造有效的防御体系,应对智能化安全威胁。

This article deeply analyzes the definition, core features, typical cases, and technical implementation of true AI-driven attacks, assisting enterprises in building effective defense systems to handle intelligent security threats.

本文深度解析Microsoft 365 Copilot的安全与合规架构,介绍其数据保护策略、身份管理机制及合规路线图,提供企业安全部署的最佳实践,助力企业安全高效地应用AI办公助手。

This article provides an in-depth analysis of Microsoft 365 Copilot's security and compliance architecture, detailing its data protection strategies, identity management mechanisms, and compliance roadmap. It offers best practices for secure deployment to help enterprises safely and efficiently leverage AI office assistants.

This article provides an in-depth analysis of the SystemBC botnet’s infection vectors, core functionalities, and defense strategies. It highlights how SystemBC infects devices via Exchange ProxyShell vulnerabilities and phishing emails to build a large proxy network. The article also recommends multi-layered defenses including patching, traffic monitoring, malicious file scanning, and access restrictions, helping enterprises detect and block SystemBC threats effectively.
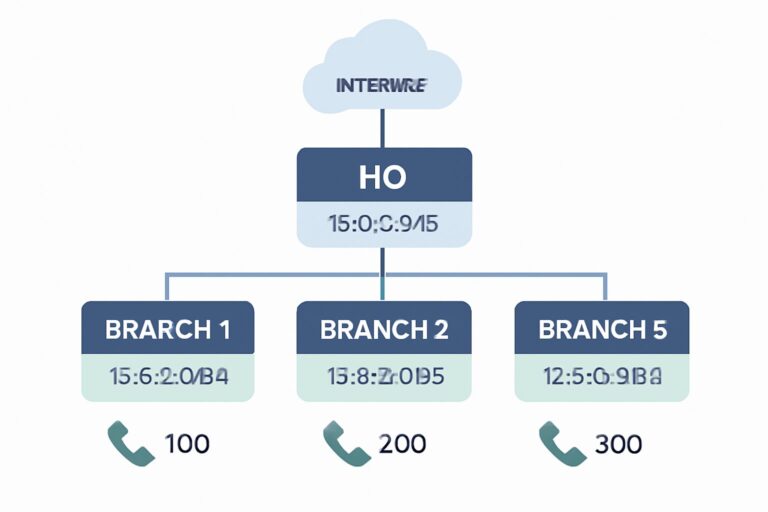
This article provides a detailed plan for internal IP address allocation and extension number management for large multi-branch enterprises, covering private address layering, flexible subnetting, route aggregation, and unified phone extension design to ensure network stability, efficiency, and scalability.
This article provides a detailed guide to safely increase Outlook PST and OST file size limits via registry and Group Policy, helping enterprises and individuals manage large mailboxes and improve efficiency.