News

How to Effectively Increase Outlook PST/OST File Size Limits: Comprehensive Guide and Practical Tips

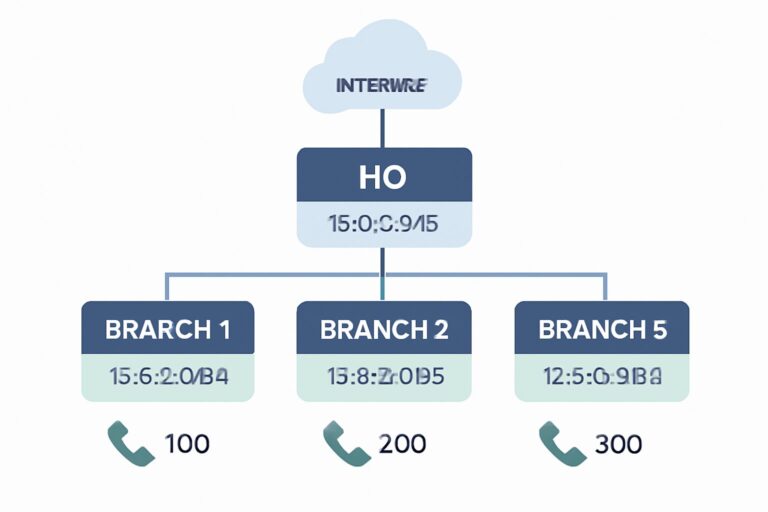
Achieving Enterprise Data Security Closed-Loop Management Using Windows Domain Controller and File Server

Windows PE USB Boot Disk Creation Guide: Step-by-Step to Build a Versatile Bootable Drive for Easy System Maintenance

Windows 11 KB5078127 Update Explained: Fixes for Outlook Attachment Issues and Printer Crashes

Comprehensive Analysis and Solutions for Modem Startup Issues Caused by Windows 11 Latest Update

Mastering Clawdbot from Zero to One: The Complete Guide to a Local AI Automation Assistant
The Crucial Role of SASE in AI Security: Protecting Your Data and Models from Threats
